Docs Home → MongoDB Compass
In-Use Encryption Connection Tab“使用中加密连接”选项卡
In-Use Encryption is an Enterprise/Atlas only feature. “使用中加密”是仅限企业/Atlas的功能。You need a replica set or sharded cluster to use this connection option. 您需要一个副本集或分片集群才能使用此连接选项。Your replica set can be a single node or larger.您的复制副本集可以是单个节点,也可以是更大的节点。
The In-Use Encryption connection tab allows you to connect your deployments with Queryable Encryption.“在线加密连接”选项卡可以使用可查询加密连接部署。
Procedure过程
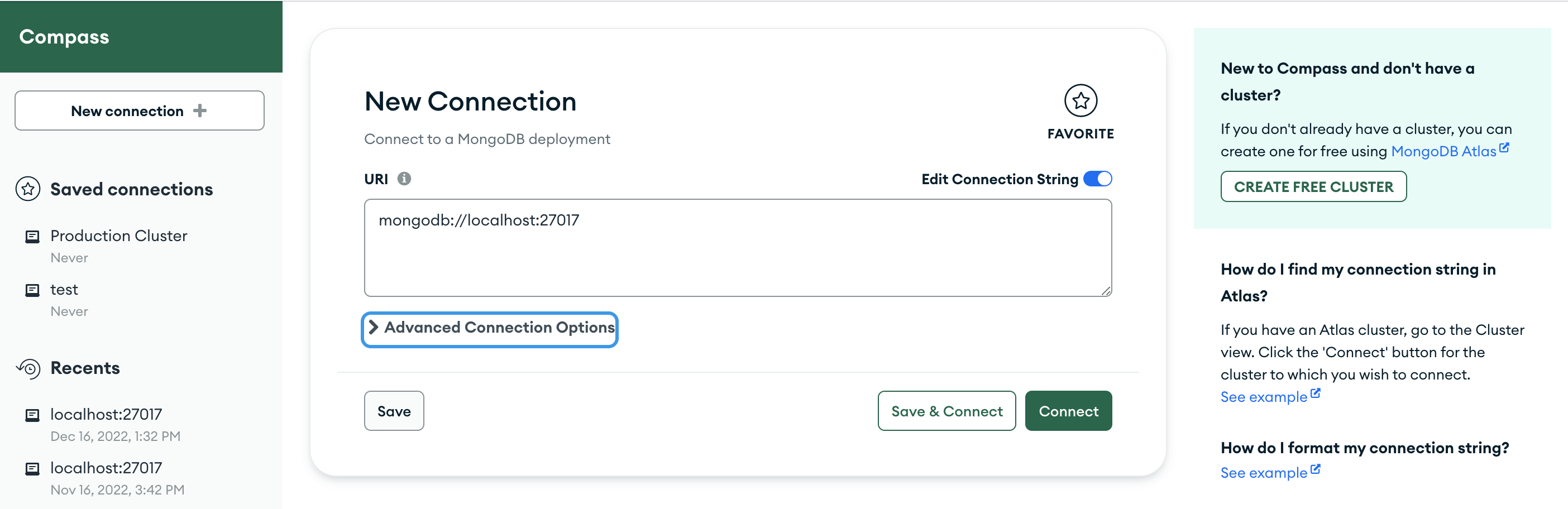
1
Click Advanced Connection Options.单击“高级连接选项”。
2
Click the In-Use Encryption tab.单击“在线加密”选项卡。
1
Provide a Key Vault Namespace.提供“密钥库命名空间”。
A Key Vault Namespace refers to a collection that contains all the data keys used for encryption and decryption.“密钥库命名空间”是指包含用于加密和解密的所有数据密钥的集合。
Specify a collection in which data encryption keys are stored in the format <db>.<collection>. 指定一个集合,其中数据加密密钥以<db>.<collection>格式存储。The non-official default database/collection for keyVault is encryption.__keyVault.keyVault的非官方默认数据库/集合是encryption.__keyVault。
2
Select a KMS Provider.选择一个“KMS提供程序”。
You can select from the following Key Management Systems:您可以从以下密钥管理系统中进行选择:
Local KMS
You can locally manage your key as a KMS using the Local KMS option.您可以使用本地KMS选项将密钥作为KMS进行本地管理。
Click Generate Random Key to generate a 96-byte long base64-encoded string. You need this key to access encrypted and decrypted data.单击“生成随机密钥”生成一个96字节长的base64编码字符串。您需要此密钥才能访问加密和解密的数据。
Warning
Compass does not save KMS credentials by default. Copy and save the key in an external location.默认情况下,Compass不会保存KMS凭据。复制密钥并将其保存在外部位置。
AWS
You can use AWS to manage your keys.您可以使用AWS来管理您的密钥。
Specify the following fields:指定以下字段:
Field字段 | Required必需 | Description描述 |
|---|
Access Key Id访问密钥Id | Yes | Value of your AWS access key Id.您的AWS访问密钥Id的值。 |
Secret Access Key秘密访问密钥 | Yes | Value of your AWS secret key.您的AWS密钥的值。 |
Session Token会话令牌 | No | Value of your AWS session token.您的AWS会话令牌的价值。 |
Certificate Authority证书颁发机构 | No | One or more certificate files from trusted Certificate Authorities to validate the certificate provided by the deployment.来自受信任证书颁发机构的一个或多个证书文件,用于验证部署提供的证书。 |
Client Certificate and Key客户端证书和密钥 | No | Specifies the location of a local .pem file that contains either the client's TLS/SSL X.509 certificate or the client's TLS/SSL certificate and key.指定本地.pem文件的位置,该文件包含客户端的TLS/SSL X.509证书或客户端的TLS/CSL证书和密钥。 |
Client Key Password客户端密钥密码 | No | If the Client Private Key is protected with a password, you must provide the password.如果客户端私钥受密码保护,则必须提供密码。 |
GCP
You can use Google Cloud Services to manage your keys.您可以使用谷歌云服务来管理您的密钥。
Specify the following fields:指定以下字段:
Field字段 | Required必需 | Description描述 |
|---|
Service Account Email服务帐户电子邮件 | Yes | The service account email to authenticate.要进行身份验证的服务帐户电子邮件。 |
Private Key私钥 | Yes | A base64-encoded private key.一个base64编码的私钥。 |
Endpoint终点 | No | A host with an optional port.具有可选端口的主机。 |
Certificate Authority证书颁发机构 | No | One or more certificate files from trusted Certificate Authorities to validate the certificate provided by the deployment.来自受信任证书颁发机构的一个或多个证书文件,用于验证部署提供的证书。 |
Client Certificate and Key客户端证书和密钥 | No | Specifies the location of a local .pem file that contains either the client's TLS/SSL X.509 certificate or the client's TLS/SSL certificate and key.指定本地.pem文件的位置,该文件包含客户端的TLS/SSL X.509证书或客户端的TLS/CSL证书和密钥。 |
Client Key Password客户端密钥密码 | No | If the Client Private Key is protected with a password, you must provide the password.如果客户端私钥受密码保护,则必须提供密码。 |
Azure
You can use Azure Key Vault to manage your keys.您可以使用Azure密钥库来管理您的密钥。
Specify the following fields:指定以下字段:
Field字段 | Required必需 | Description描述 |
|---|
| Tenant Id | Yes | Identifies the organization for the account.标识帐户的组织。 |
| Client Id | Yes | Authenticates a registered application.对已注册的应用程序进行身份验证。 |
Client Secret客户端机密 | Yes | The client secret to authenticate a registered application.用于验证已注册应用程序的客户端机密。 |
Identity Platform Endpoint身份平台终结点 | Yes | A host with an optional port.具有可选端口的主机。 |
Certificate Authority证书颁发机构 | No | One or more certificate files from trusted Certificate Authorities to validate the certificate provided by the deployment.来自受信任证书颁发机构的一个或多个证书文件,用于验证部署提供的证书。 |
Client Certificate and Key客户端证书和密钥 | No | Specifies the location of a local .pem file that contains either the client's TLS/SSL X.509 certificate or the client's TLS/SSL certificate and key.指定本地pem文件的位置,该文件包含客户端的TLS/SSL X.509证书或客户端的TLS/CSL证书和密钥。 |
Client Key Password客户端密钥密码 | No | If the Client Private Key is protected with a password, you must provide the password.如果客户端私钥受密码保护,则必须提供密码。 |
KMIP
You can use KMIP to manage your keys.您可以使用KMIP来管理您的密钥。
Field字段 | Required必需 | Description描述 |
|---|
Endpoint终点 | Yes | The endpoint consists of a hostname and port separated by a colon.端点由主机名和端口组成,端口之间用冒号分隔。 |
Certificate Authority证书颁发机构 | No | One or more certificate files from trusted Certificate Authorities to validate the certificate provided by the deployment.来自受信任证书颁发机构的一个或多个证书文件,用于验证部署提供的证书。 |
Client Certificate and Key客户端证书和密钥 | No | Specifies the location of a local .pem file that contains either the client's TLS/SSL X.509 certificate or the client's TLS/SSL certificate and key.指定本地.pem文件的位置,该文件包含客户端的TLS/SSL X.509证书或客户端的TLS/CSL证书和密钥。 |
Client Key Password客户端密钥密码 | No | If the Client Private Key is protected with a password, you must provide the password.如果客户端私钥受密码保护,则必须提供密码。 |
3
(Optional) Specify an EncryptedFieldsMap(可选)指定加密字段映射
Add an optional client-side EncryptedFieldsMap for enhanced security.添加可选的客户端EncryptedFieldsMap以增强安全性。
For more information, see Fields for Encryption.有关详细信息,请参阅加密字段。