Options选项
On this page本页内容
Use the following options to control various aspects of your MongoDB Shell connection and behavior.使用以下选项可以控制MongoDB Shell连接和行为的各个方面。
General Options常规选项
--build-info-
Returns a JSON-formatted document with information about the返回一个JSON格式的文档,其中包含有关mongoshbuild.mongosh构建的信息。
--eval <javascript>-
Evaluates a JavaScript expression. You can use a single评估JavaScript表达式。可以使用单个--evalargument or multiple--evalarguments together.--eval参数,也可以同时使用多个--eval参数。Aftermongoshevaluates the--evalargument, it prints the results to your command line.mongosh对--eval参数求值后,会将结果打印到命令行中。If you use multiple如果使用多个--evalstatements,mongoshonly prints the results of the last--eval.--eval语句,mongosh只打印最后一个--eval的结果。Example: Format Output
To get output suitable for automated parsing, use要获得适合自动解析的输出,请使用EJSON.stringify().EJSON.stringify()。mongosh --quiet --host rs0/centos1104 --port 27500 \
--eval "EJSON.stringify(rs.status().members.map( \
m => ({'id':m._id, 'name':m.name, 'stateStr':m.stateStr})));" \
| jqAfter parsing with使用jq, the output resembles this:jq进行解析后,输出类似于以下内容:[
{
"id": 0,
"name": "centos1104:27500",
"stateStr": "PRIMARY"
},
{
"id": 1,
"name": "centos1104:27502",
"stateStr": "SECONDARY"
},
{
"id": 2,
"name": "centos1104:27503",
"stateStr": "SECONDARY"
}
]NoteEJSONhas built in formatting options which may eliminate the need for a parser likejq. For example, the following code produces output that is formatted the same as above.EJSON内置了格式化选项,可以消除对像jq这样的解析器的需求。例如,下面的代码生成的输出格式与上面相同。mongosh --quiet --host rs0/centos1104 --port 27500 \
--eval "EJSON.stringify( rs.status().members.map( \
({ _id, name, stateStr }) => ({ _id, name, stateStr })), null, 2);"Example: Multiple ``--eval`` Arguments
To get a list of collections in the要在moviesDatabase, use multiple--evalstatements:moviesDatabase中获取集合列表,请使用多个--eval语句:mongosh --quiet \
--eval 'use moviesDatabase' \
--eval 'show collections' \
mongodb://localhost/
--help, -h-
Returns information on the options and use of the MongoDB Shell.返回有关MongoDB Shell的选项和使用的信息。
--nodb-
Prevents the shell from connecting to any database instances.阻止外壳程序连接到任何数据库实例。
--norc-
Prevents the shell from sourcing and evaluating阻止shell在启动时查找和评估~/.mongoshrc.json startup.~/.mongoshrc.js。
--quiet-
Skips all messages during startup (such as welcome messages and startup warnings) and goes directly to the prompt.在启动过程中跳过所有消息(如欢迎消息和启动警告),然后直接进入提示。
--shell-
Enables the shell interface.启用外壳程序界面。If you invoke the如果调用mongoshcommand and specify a JavaScript file as an argument, or use--evalto specify JavaScript on the command line, the--shelloption provides the user with a shell prompt after the file finishes executing.mongosh命令并指定一个JavaScript文件作为参数,或者在命令行中使用--eval指定JavaScript,那么在文件执行完成后,--shell选项将为用户提供shell提示。
--verbose-
Increases the verbosity of the shell output during the connection process and when running commands.在连接过程中和运行命令时增加shell输出的详细程度。
--version-
Returns the MongoDB Shell release number.返回MongoDB Shell版本号。
Stable API Options稳定的API选项
--apiVersion <version number>-
Specifies the apiVersion.指定apiVersion。"1"is currently the only supported value."1"是当前唯一支持的值。
--apiStrict-
Specifies that the server will respond with APIStrictError if your application uses a command or behavior outside of the Stable API.指定如果应用程序使用Stable API之外的命令或行为,则服务器将使用APIStrictError进行响应。If you specify如果指定--apiStrict, you must also specify--apiVersion.--apiStrict,则还必须指定--apiVersion。
--apiDeprecationErrors-
Specifies that the server will respond with APIDeprecationError if your application uses a command or behavior that is deprecated in the specified指定如果应用程序使用的命令或行为在指定的apiVersion.apiVersion中已弃用,则服务器将使用APIDeprecationError进行响应。If you specify如果指定--apiDeprecationErrors, you must also specify--apiVersion.--apiDeprecationErrors,则还必须指定--apiVersion。
Connection Options连接选项
--host <hostname>-
Specifies the name of the host machine where the指定运行mongodormongosis running.mongod或mongos的主机的名称。If this is not specified, the MongoDB Shell attempts to connect to a MongoDB process running on the localhost.如果未指定,MongoDB Shell将尝试连接到本地主机上运行的MongoDB进程。To connect to a replica set,为了连接到副本集,-
Specify the指定副本集名称和集成员的种子列表。replica set nameand a seed list of set members.Use the following form:使用以下表格:<replSetName>/<hostname1><:port>,<hostname2><:port>,<...>
For TLS/SSL connections (对于TLS/SSL连接(--tls),--tls),The MongoDB Shell shell verifies that the hostname (specified in theMongoDB Shell Shell验证主机名(在--hostoption or the connection string) matches theSAN(or, ifSANis not present, theCN) in the certificate presented by themongodormongos.--host选项或连接字符串中指定)是否与mongod或mongos提供的证书中的SAN(或者,如果不存在SAN,则为CN)匹配。If如果存在SANis present, the MongoDB Shell does not match against theCN.SAN,则MongoDB Shell与CN不匹配。If the hostname does not match the如果主机名与SAN(或CN)不匹配,则MongoDB Shell外壳无法连接。SAN(orCN), the MongoDB Shell shell fails to connect.
For DNS seedlist connections,对于DNS种子列表连接,-
Specify the connection protocol as将连接协议指定为mongodb+srv, followed by the DNS SRV hostname record and any options.mongodb+srv,然后指定DNS srv主机名记录和任何选项。TheauthSourceandreplicaSetoptions, if included in the connection string, overrides any corresponding DNS-configured options set in the TXT record.authSource和replicaSet选项(如果包含在连接字符串中)将覆盖TXT记录中设置的任何相应的DNS配置选项。Use of the使用mongodb+srv:connection string implicitly enables TLS / SSL (normally set withtls=true) for the client connection.mongodb+srv:连接字符串会隐式启用客户端连接的TLS/SSL(通常设置为TLS=true)。The TLS option can be turned off by setting可以通过在查询字符串中设置tls=falsein the query string.TLS=false来关闭TLS选项。mongodb+srv://server.example.com/?connectionTimeout=3000ms
--port <port>-
Specifies the port where the指定mongodormongosinstance is listening.mongod或mongos实例正在侦听的端口。If如果没有指定--portis not specified, the MongoDB Shell attempts to connect to port27017.--port,MongoDB Shell将尝试连接到27017端口。
TLS OptionsTLS选项
--tls-
Enables connection to a启用到已启用TLS/SSL支持的mongodormongosthat has TLS / SSL support enabled.mongod或mongos的连接。To learn more about TLS/SSL and MongoDB, see:要了解有关TLS/SSL和MongoDB的更多信息,请参阅:
--tlsCertificateKeyFile <filename>-
Specifies the指定包含.pemfile that contains both the TLS / SSL certificate and key formongosh.mongosh的TLS/SSL证书和密钥的.pem文件。Specify the file name of the使用相对路径或绝对路径指定pem文件的文件名。.pemfile using relative or absolute paths.This option is required when using the当使用--tlsoption to connect to amongodormongosinstance that requires client certificates.--tls选项连接到需要客户端证书的mongod或mongos实例时,需要此选项。That is, the MongoDB Shell presents this certificate to the server.也就是说,MongoDB Shell将此证书提供给服务器。NoteTo learn more about TLS/SSL and MongoDB, see:要了解有关TLS/SSL和MongoDB的更多信息,请参阅:
--tlsCertificateKeyFilePassword <value>-
Specifies the password to de-crypt the certificate-key file (i.e.指定对证书密钥文件(即--tlsCertificateKeyFile).--tlsCertificateKeyFile)进行解密的密码。Use the仅当证书密钥文件已加密时,才使用--tlsCertificateKeyFilePasswordoption only if the certificate-key file is encrypted. In all cases, the MongoDB Shell redacts the password from all logging and reporting output.--tlsCertificateKeyFilePassword选项。在所有情况下,MongoDB Shell都会对所有日志记录和报告输出中的密码进行编辑。If the private key in the PEM file is encrypted and you do not specify the如果PEM文件中的私钥是加密的,并且您没有指定--tlsCertificateKeyFilePasswordoption; the MongoDB Shell prompts for a passphrase.--tlsCertificateKeyFilePassword选项;MongoDB Shell会提示输入密码短语。See TLS/SSL Certificate Passphrase.请参阅TLS/SSL证书密码短语。To learn more about TLS/SSL and MongoDB, see:要了解有关TLS/SSL和MongoDB的更多信息,请参阅:
--tlsCAFile <filename>-
Specifies the指定包含证书颁发机构的根证书链的.pemfile that contains the root certificate chain from the Certificate Authority..pem文件。This file is used to validate the certificate presented by the此文件用于验证mongod/mongosinstance.mongod/mongos实例提供的证书。Specify the file name of the使用相对路径或绝对路径指定.pemfile using relative or absolute paths..pem文件的文件名。To learn more about TLS/SSL and MongoDB, see:要了解有关TLS/SSL和MongoDB的更多信息,请参阅:
--tlsCRLFile <filename>-
Specifies the指定包含证书吊销列表的.pemfile that contains the Certificate Revocation List..pem文件。Specify the file name of the使用相对路径或绝对路径指定.pemfile using relative or absolute paths..pem文件的文件名。To learn more about TLS/SSL and MongoDB, see:要了解有关TLS/SSL和MongoDB的更多信息,请参阅:
--tlsAllowInvalidHostnames-
Disables the validation of the hostnames in the certificate presented by the禁用验证mongod/mongosinstance.mongod/mongos实例提供的证书中的主机名。Allows the MongoDB Shell to connect to MongoDB instances even if the hostname in the server certificates do not match the server's host.允许MongoDB Shell连接到MongoDB实例,即使服务器证书中的主机名与服务器的主机不匹配。To learn more about TLS/SSL and MongoDB, see:要了解有关TLS/SSL和MongoDB的更多信息,请参阅:
--tlsAllowInvalidCertificatesNew in version 4.2.4.2版新增。Bypasses the validation checks for the certificates presented by the绕过对mongod/mongosinstance and allows connections to servers that present invalid certificates.mongod/mongos实例提供的证书的验证检查,并允许连接到提供无效证书的服务器。NoteStarting in MongoDB 4.0, if you specify从MongoDB 4.0开始,如果在使用x.509身份验证时指定--tlsAllowInvalidCertificateswhen using x.509 authentication, an invalid certificate is only sufficient to establish a TLS / SSL connection but is insufficient for authentication.--tlsAllowInvalidCertificates,则无效证书仅足以建立TLS/SSL连接,但不足以进行身份验证。WarningAlthough available, avoid using the尽管可用,但如果可能,请避免使用--tlsAllowInvalidCertificatesoption if possible.--tlsAllowInvalidCertificates选项。If the use of如果需要使用--tlsAllowInvalidCertificatesis necessary, only use the option on systems where intrusion is not possible.--tlsAllowInvalidCertificates,请仅在不可能进行入侵的系统上使用该选项。If the MongoDB Shell shell (and other MongoDB Tools) runs with the如果MongoDB Shell Shell(和其他MongoDB工具)使用--tlsAllowInvalidCertificatesoption, the shell (and other MongoDB Tools) do not attempt to validate the server certificates.--tlsAllowInvalidCertificates选项运行,则Shell(和其它MongoDB工具)不会尝试验证服务器证书。This creates a vulnerability to expired这会对过期的mongodandmongoscertificates as well as to foreign processes posing as validmongodormongosinstances.mongod和mongos证书以及冒充有效mongod或mongos实例的外部进程造成漏洞。If you only need to disable the validation of the hostname in the TLS / SSL certificates, see如果只需要禁用TLS/SSL证书中主机名的验证,请参阅--tlsAllowInvalidHostnames.--tlsAllowInvalidHostnames。To learn more about TLS/SSL and MongoDB, see:要了解有关TLS/SSL和MongoDB的更多信息,请参阅:
--tlsCertificateSelector <parameter>=<value>-
Available on Windows and macOS as an alternative to可在Windows和macOS上作为--tlsCertificateKeyFile.--tlsCertificateKeyFile的替代方案使用。ImportantWindows and Importing Private KeysWindows和导入私钥When you import your private key, you must mark it as exportable.导入私钥时,必须将其标记为可导出。The Windows Certificate Import Wizard doesn't check this option by default.默认情况下,Windows证书导入向导不会选中此选项。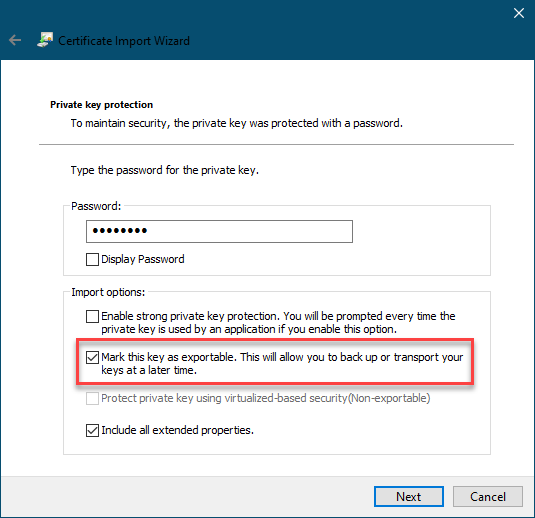
The--tlsCertificateKeyFileand--tlsCertificateSelectoroptions are mutually exclusive.--tlsCertificateKeyFile和--tlsCertificateSelector选项是互斥的。You can only specify one.您只能指定一个。Specifies a certificate property in order to select a matching certificate from the operating system's certificate store.指定证书属性,以便从操作系统的证书存储中选择匹配的证书。--tlsCertificateSelectoraccepts an argument of the format接受格式为<property>=<value>where the property can be one of the following:<property>=<value>的参数,其中该属性可以是以下内容之一:Property所有物Value type值类型Description描述subjectASCII string Subject name or common name on certificate证书上的使用者名称或通用名称thumbprinthex string A sequence of bytes, expressed as hexadecimal, used to identify a public key by its SHA-1 digest.一种字节序列,用十六进制表示,用于通过SHA-1摘要识别公钥。
Thethumbprintis sometimes referred to as afingerprint.thumbprint有时被称为fingerprint。When using the system SSL certificate store, OCSP (Online Certificate Status Protocol) is used to validate the revocation status of certificates.使用系统SSL证书存储时,OCSP(联机证书状态协议)用于验证证书的吊销状态。
--tlsDisabledProtocols <string>-
Disables the specified TLS protocols. The option recognizes the following protocols:禁用指定的TLS协议。该选项可识别以下协议:TLS1_0TLS1_1TLS1_2(Starting in version 4.0.4, 3.6.9, 3.4.24)(从版本4.0.4、3.6.9、3.4.24开始)TLS1_3On macOS, you cannot disable在macOS上,不能禁用TLS1_1and leave bothTLS1_0andTLS1_2enabled.TLS1_1并同时启用TLS1_0和TLS1_2。You must also disable at least one of the other two; for example,您还必须禁用其他两个中的至少一个;例如TLS1_0,TLS1_1.TLS1_0、TLS1_1。To list multiple protocols, specify as a comma separated list of protocols.要列出多个协议,请指定为以逗号分隔的协议列表。For example例如TLS1_0,TLS1_1.TLS1_0、TLS1_1。The specified disabled protocols overrides any default disabled protocols.指定的禁用协议将覆盖任何默认的禁用协议。
Starting in version 4.0, MongoDB disables the use of TLS 1.0 if TLS 1.1+ is available on the system.从4.0版本开始,如果TLS 1.1+在系统上可用,MongoDB将禁用TLS 1.0的使用。To enable the disabled TLS 1.0, specify若要启用禁用的TLS 1.0,请将noneto--tlsDisabledProtocols.none指定为--tlsDisabledProtocols。
--tlsUseSystemCA-
Allows允许mongoshto load TLS certificates available to the operating system's certificate authority.mongosh加载操作系统证书颁发机构可用的TLS证书。Use this option if you want to use TLS certificates already available to your operating system without explicitly specifying those certificates to如果您希望使用操作系统已可用的TLS证书,而不将这些证书明确指定给mongosh.mongosh,请使用此选项。
Authentication Options身份验证选项
--authenticationDatabase <dbname>-
Specifies the authentication database where the specified指定创建指定的--usernamehas been created.--username的身份验证数据库。See Authentication Database.请参阅身份验证数据库。If you do not specify a value for如果没有为--authenticationDatabase, the MongoDB Shell uses the database specified in the connection string.--authenticationDatabase指定值,MongoDB Shell将使用连接字符串中指定的数据库。
--authenticationMechanism <name>-
Specifies the authentication mechanism the MongoDB Shell uses to authenticate to the指定MongoDB Shell用于向mongodormongos.mongod或mongos进行身份验证的身份验证机制。If you don't specify an如果您没有指定authenticationMechanismbut provide user credentials, the MongoDB Shell and drivers attempt to use SCRAM-SHA-256. If this fails, they fall back to SCRAM-SHA-1.authenticationMechanism,但提供了用户凭据,MongoDB Shell和驱动程序会尝试使用SCRAM-SHA-256。如果失败,则返回SCRAM-SHA-1。Value值Description描述SCRAM-SHA-1 RFC 5802 standard Salted Challenge Response Authentication Mechanism using the SHA-1 hash function.使用SHA-1散列函数的标准Salted质询-响应认证机制。SCRAM-SHA-256 RFC 7677 standard Salted Challenge Response Authentication Mechanism using the SHA-256 hash function.使用SHA-256散列函数的标准Salted质询-响应认证机制。
Requires featureCompatibilityVersion set to需要将4.0.featureCompatibilityVersion设置为4.0。MONGODB-X509 MongoDB TLS / SSL certificate authentication.MongoDBTLS/SSL证书身份验证。GSSAPI (Kerberos) External authentication using Kerberos.使用Kerberos的外部身份验证。This mechanism is available only in MongoDB Enterprise此机制仅在MongoDB Enterprise中可用。.
PLAIN (LDAP SASL) External authentication using LDAP.使用LDAP的外部身份验证。You can also use您还可以使用PLAINfor authenticating in-database users.PLAIN对数据库中的用户进行身份验证。PLAINtransmits passwords in plain text.PLAIN以纯文本形式传输密码。This mechanism is available only in MongoDB Enterprise此机制仅在MongoDB Enterprise中可用。.
--gssapiServiceName-
Specify the name of the service using GSSAPI/Kerberos.使用GSSAPI/Kerberos指定服务的名称。Only required if the service does not use the default name of仅当服务未使用mongodb的默认名称时才需要。mongodb.This option is available only in MongoDB Enterprise.此选项仅在MongoDB Enterprise中可用。
--sspiHostnameCanonicalization <string>-
Specifies whether or not to use Hostname Canonicalization.指定是否使用主机名规范化。--sspiHostnameCanonicalizationhas the same effect as setting the具有与在连接字符串的CANONICALIZE_HOST_NAME:true|falsekey-pair in theauthMechanismPropertiesportion of the connection string.authMechanismProperties部分中设置CANONICALIZE_HOST_NAME:true|false密钥对相同的效果。If如果--sspiHostnameCanonicalizationis set to:--sspiHostnameCanonicalization设置为:forwardAndReverse, performs a forward DNS lookup and then a reverse lookup.,执行正向DNS查找,然后执行反向查找。New inmongosh1.3.0.forward, the effect is the same as setting,效果与设置authMechanismProperties=CANONICALIZE_HOST_NAME:true.authMechanismProperties=CANONICALIZE_HOST_NAME:true相同。none, the effect is the same as setting,效果与设置authMechanismProperties=CANONICALIZE_HOST_NAME:false.authMechanismProperties=CANONICALIZE_HOST_NAME:false相同。
--password <password>, -p <password>-
Specifies a password with which to authenticate to a MongoDB database that uses authentication.指定用于向使用身份验证的MongoDB数据库进行身份验证的密码。Use in conjunction with the与--usernameand--authenticationDatabaseoptions.--username和--authenticationDatabase选项一起使用。To force the MongoDB Shell to prompt for a password, enter the要强制MongoDB Shell提示输入密码,请输入--passwordoption as the last option and leave out the argument.--password选项作为最后一个选项,并省略参数。
--username <username>, -u <username>-
Specifies a username with which to authenticate to a MongoDB database that uses authentication.指定用于向使用身份验证的MongoDB数据库进行身份验证的用户名。Use in conjunction with the与--passwordand--authenticationDatabaseoptions.--password和--authenticationDatabase选项一起使用。
Session Options会话选项
--retryWrites-
Enables Retryable Writes.启用可重试写入。Retryable writes are enabled by default inmongosh.mongosh中默认启用可重试写入。Retryable writes are disabled by default in the legacy在传统mongo shell中,默认情况下禁用可重试写入。mongoshell.To disable retryable writes, use若要禁用可重试写入,请使用--retryWrites=false.--retryWrites=false。For more information on sessions, see Client Sessions and Causal Consistency Guarantees.有关会话的更多信息,请参阅客户端会话和因果一致性保证。
Client-Side Field Level Encryption Options客户端字段级加密选项
--awsAccessKeyId <string>-
An AWS Access Key与IAM用户关联的AWS访问密钥associated with an IAM user who has
ListandReadpermissions for the AWS Key Management Service (KMS).,IAM用户具有AWS密钥管理服务(KMS)的
List和Read权限。mongoshuses the specified--awsAccessKeyIdto access the KMS.mongosh使用指定的--awsAccessKeyId访问KMS。--awsAccessKeyIdis required to enable Client-Side Field Level Encryption for themongoshshell session.--awsAccessKeyId是为mongoshshell会话启用客户端字段级加密所必需的。--awsAccessKeyIdrequires both of the following command line options:需要以下两个命令行选项:If如果省略了--awsAccessKeyIdis omitted, use theMongo()constructor within the shell session to enable client-side field level encryption.--awsAccessKeyId,请在shell会话中使用Mongo()构造函数来启用客户端字段级加密。To mitigate the risk of leaking access keys into logs, consider specifying an environmental variable to要降低将访问密钥泄漏到日志中的风险,请考虑将环境变量指定为--awsAccessKeyId.--awsAccessKeyId。
--awsSecretAccessKey <string>-
An AWS Secret Key与指定的associated to the specified
--awsAccessKeyId.--awsAccessKeyId.关联的AWS密钥。
--awsSecretAccessKeyis required to enable Client-Side Field Level Encryption for themongoshsession.--awsSecretAccessKey是为mongosh会话启用客户端字段级加密所必需的。--awsSecretAccessKeyrequires both of the following command line options:--awsSecretAccessKey需要以下两个命令行选项:If如果省略了--awsSecretAccessKeyand its supporting options are omitted, useMongo()within the shell session to enable client-side field level encryption.--awsSecretAccessKey及其支持选项,请在shell会话中使用Mongo()来启用客户端字段级加密。To mitigate the risk of leaking access keys into logs, consider specifying an environmental variable to要降低将访问密钥泄漏到日志中的风险,请考虑将环境变量指定为--awsSecretAccessKey.--awsSecretAccessKey。
--awsSessionToken <string>-
An AWS Session Token与指定的associated to the specified
--awsAccessKeyId.--awsAccessKeyId关联的AWS会话令牌。
--awsSessionTokenis required to enable Client-Side Field Level Encryption for themongoshshell session.--awsSessionToken是为mongoshshell会话启用客户端字段级加密所必需的。--awsSessionTokenrequires all of the following command line options:需要以下所有命令行选项:If如果省略了--awsSessionTokenand its supporting options are omitted, useMongo()within the shell session to enable client-side field level encryption.--awsSessionToken及其支持选项,请在shell会话中使用Mongo()来启用客户端字段级加密。To mitigate the risk of leaking access keys into logs, consider specifying an environmental variable to要降低将访问密钥泄漏到日志中的风险,请考虑为--awsSessionToken.--awsSessionToken指定一个环境变量。
--keyVaultNamespace <string>-
The full namespace (用作客户端字段级加密的密钥保管库的集合的完整命名空间(<database>.<collection>) of the collection used as a key vault for Client-Side Field Level Encryption.<database>.<collection>)。--keyVaultNamespaceis required for enabling client-side field level encryption.--keyVaultNamespace是启用客户端字段级加密所必需的。for the用于mongoshshell session.mongoshshell会话。mongoshcreates the specified namespace if it does not exist.如果指定的命名空间不存在,则创建该命名空间。--keyVaultNamespacerequires both of the following command line options:--keyVaultNamespace需要以下两个命令行选项:If如果省略了--keyVaultNamespaceand its supporting options are omitted, use theMongo()constructor within the shell session to enable client-side field level encryption.--keyVaultNamespace及其支持选项,请在shell会话中使用Mongo()构造函数来启用客户端字段级加密。