Features功能
On this page本页内容
Overview概述
On this page, you can learn about the security benefits of Queryable Encryption, how it works, and how it compares to other security mechanisms supported by MongoDB. 在这个页面上,您可以了解可查询加密的安全优势,它是如何工作的,以及它与MongoDB支持的其他安全机制的比较。You can also view a fictional scenario that demonstrates the value of Queryable Encryption in securing your data.您还可以查看一个虚构的场景,该场景演示了可查询加密在保护数据安全方面的价值。
Queryable Encryption可查询加密
Queryable Encryption enables a client application to encrypt data before transporting it over the network using fully randomized encryption, while maintaining queryability. Sensitive data is transparently encrypted and decrypted by the client and only communicated to and from the server in encrypted form.可查询加密使客户端应用程序能够在使用完全随机加密通过网络传输数据之前对数据进行加密,同时保持可查询性。敏感数据由客户端透明地加密和解密,并且仅以加密的形式与服务器通信。
Unlike Client-Side Field Level Encryption that can use Deterministic Encryption, Queryable Encryption uses fast, searchable encryption schemes based on Structured Encryption与可以使用确定性加密的客户端字段级加密不同,可查询加密使用基于结构化加密的快速、可搜索的加密方案。即使给定相同的明文输入,这些方案也会产生不同的加密输出值。. These schemes produce different encrypted output values even when given the same cleartext input.
How Queryable Encryption Works可查询加密的工作原理
The diagram below shows the process and architecture of how Queryable Encryption is used in a customer environment.下图显示了如何在客户环境中使用可查询加密的过程和体系结构。
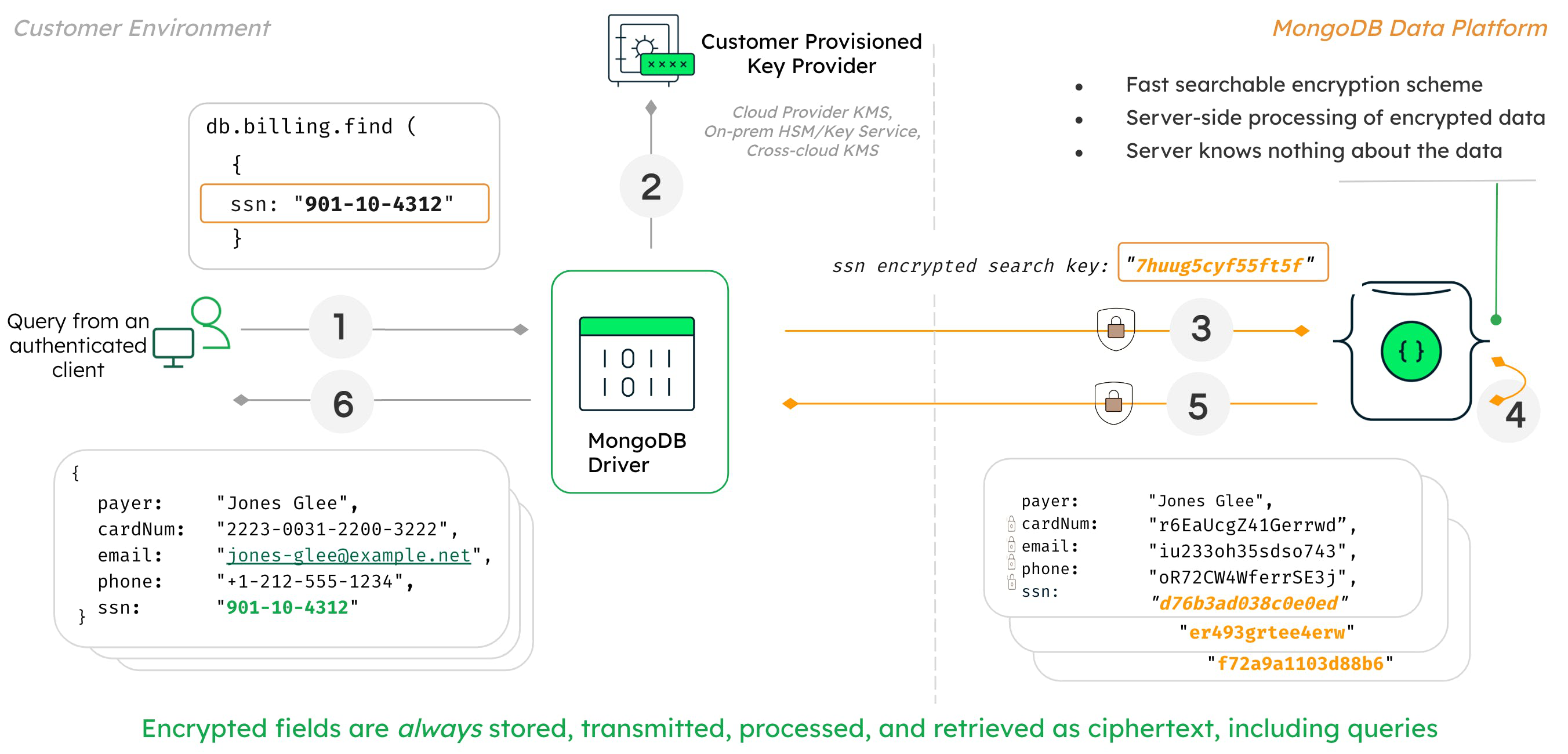
In this diagram, the user is able to query on fully randomly encrypted data such as SSN number.在该图中,用户能够查询完全随机加密的数据,例如SSN号码。
The process and mechanisms that make this possible within Queryable Encryption are as follows:在可查询加密中实现这一点的过程和机制如下:
When the application submits the query, MongoDB drivers first analyze the query.当应用程序提交查询时,MongoDB驱动程序首先分析查询。The driver recognizes the query is against an encrypted field and requests the encryption keys from the customer-provisioned key provider such as:驱动程序识别出查询是针对加密字段的,并向客户提供的键提供商请求加密键,例如:- AWS Key Management Service (AWS KMS)
- Google Cloud KMS
- Azure Key Vault
Any KMIP-compliant key provider任何符合KMIP的键提供程序
The driver submits the query to the MongoDB server with the encrypted fields rendered as ciphertext.驱动程序将查询提交给MongoDB服务器,并将加密字段呈现为密文。Queryable Encryption implements a fast, searchable scheme that allows the server to process queries on fully encrypted data, without knowing anything about the data. The data and the query itself remain encrypted at all times on the server.可查询加密实现了一种快速、可搜索的方案,允许服务器在不了解任何数据的情况下处理对完全加密数据的查询。数据和查询本身在服务器上始终保持加密状态。The MongoDB server returns the encrypted results of the query to the driver.MongoDB服务器将加密的查询结果返回给驱动程序。The query results are decrypted with the keys held by the driver and returned to the client and shown as plaintext.查询结果使用驱动程序持有的键进行解密,并返回给客户端,以明文形式显示。
Queryable Encryption functions with the help of the following data structures. It is critical that these are not modified or deleted, or query results will be incorrect.可查询加密在以下数据结构的帮助下发挥作用。至关重要的是,不要修改或删除这些内容,否则查询结果将不正确。
Queryable Encryption adds a可查询加密将__safeContent__field to documents in any collection where there's a Queryable Encryption encrypted field.__safeContent__字段添加到任何集合中有可查询加密加密字段的文档中。Queryable Encryption creates two internal metadata collections in the same database as the collection where there's a Queryable Encryption encrypted field. These are named as follows:可查询加密在同一数据库中创建两个内部元数据集合,该集合中有一个可查询加密加密字段。它们的名称如下:enxcol_.<collectionName>.escenxcol_.<collectionName>.ecoc
Do not modify these data structures or query results will be incorrect and security could be impacted.不要修改这些数据结构,否则查询结果将不正确,安全性可能受到影响。
Queryable Encryption keeps encrypted fields secure in the following scenarios:可查询加密在以下情况下保持加密字段的安全:
Direct access to encrypted fields by a database superuser数据库超级用户对加密字段的直接访问Access to encrypted fields by reading the server's memory通过读取服务器内存访问加密字段Capture of encrypted fields over an insecure network通过不安全的网络捕获加密字段Access to on-disk encrypted fields by reading database or backup files通过读取数据库或备份文件访问磁盘上加密的字段Frequency analysis attacks by identifying patterns in documents with encrypted fields通过识别具有加密字段的文档中的模式进行频率分析攻击
While all clients have access to the non-sensitive data fields, only appropriately-configured Queryable Encryption clients are able to run read and write queries using the encrypted data fields.虽然所有客户端都可以访问非敏感数据字段,但只有经过适当配置的可查询加密客户端才能使用加密的数据字段运行读写查询。
Remote Key Management System远程键管理系统
When you use Queryable Encryption in production, you must use a remote Key Management System (KMS) to store your encryption key.在生产中使用可查询加密时,必须使用远程键管理系统(KMS)来存储加密键。
To view a step-by-step guide demonstrating how to use a remote KMS with Queryable Encryption, see Tutorials.要查看演示如何使用可查询加密的远程KMS的分步指南,请参阅教程。
To view a list of all supported KMS providers, see KMS Providers.要查看所有受支持的KMS提供程序的列表,请参阅KMS提供器。
To learn more about why you should use a remote KMS, see Reasons to Use a Remote Key Management System.要了解有关为什么应该使用远程KMS的更多信息,请参阅使用远程键管理系统的原因。
Other Security Mechanisms其他安全机制
This section describes the following security mechanisms supported by MongoDB and explains their use cases and limitations:本节介绍了MongoDB支持的以下安全机制,并解释了它们的用例和限制:
Role-Based Access Control基于角色的访问控制Encryption at Rest静止时的加密Transport Encryption (TLS/SSL)传输加密(TLS/SSL)
Role-Based Access Control基于角色的访问控制
Role-Based Access Control is a security mechanism that allows administrators to grant and restrict collection-level permissions for users. With the appropriate role definition and assignment, this solution prevents accidental disclosure of data and access.基于角色的访问控制是一种安全机制,允许管理员为用户授予和限制集合级别的权限。通过适当的角色定义和分配,此解决方案可以防止意外泄露数据和访问。
Role-Based Access control cannot protect against the following scenarios:基于角色的访问控制无法防范以下情况:
Capture of the data over an insecure network通过不安全的网络捕获数据Access to on-disk data by reading database or backup files通过读取数据库或备份文件访问磁盘上的数据Access to data by reading the server's memory通过读取服务器内存访问数据Direct access to data by a database superuser数据库超级用户直接访问数据
To learn more, see Role-Based Access Control.要了解更多信息,请参阅基于角色的访问控制。
Encryption at Rest静止时的加密
Encryption at Rest is a mechanism that encrypts database files on disk. 静止加密是一种对磁盘上的数据库文件进行加密的机制。This mechanism prevents a person who lacks database credentials, but has access to the computer hosting your database, from viewing your data.此机制可防止缺少数据库凭据但有权访问承载数据库的计算机的人查看您的数据。
This mechanism does not protect your data against the following scenarios:此机制无法保护您的数据免受以下情况的影响:
Capture of the data over an insecure network通过不安全的网络捕获数据Access to data by reading the server's memory通过读取服务器内存访问数据Direct access to data by a database superuser数据库超级用户直接访问数据
To learn more, see Encryption at Rest.要了解更多信息,请参阅静止加密。
Transport Encryption (TLS/SSL)传输加密(TLS/SSL)
Transport Encryption using TLS/SSL encrypts your data over the network. 使用TLS/SSL的传输加密通过网络加密您的数据。TLS/SSL protects your data as it travels over an insecure network, but cannot protect your data from a privileged user or as it sits on disk.TLS/SSL在数据在不安全的网络上传输时保护您的数据,但不能保护数据不受权限用户或磁盘上的数据的影响。
To learn more, see Transport Encryption using TLS/SSL要了解更多信息,请参阅使用TLS/SSL的传输加密
Comparison of Features特性比较
The following diagram describes security features MongoDB supports and the potential security vulnerabilities that they address:下图描述了MongoDB支持的安全功能及其解决的潜在安全漏洞:
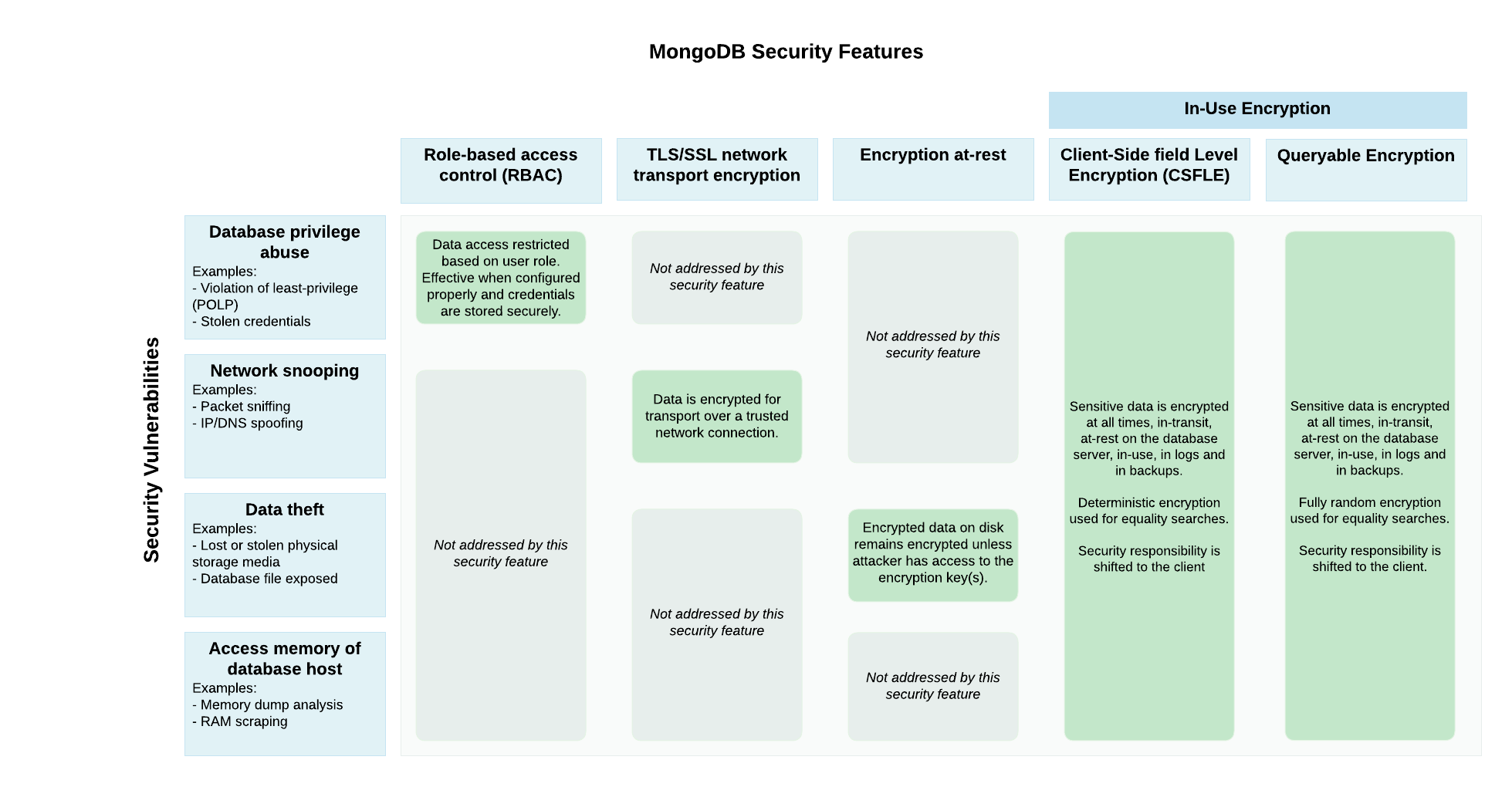
Use the Mechanisms Together一起使用这些机制
To secure a production deployment, use Role-Based Access Control, Encryption at Rest, Transport Encryption, and optionally, the In-Use Encryption security mechanisms together. Please note that you cannot use both Client-Side Field Level Encryption and Queryable Encryption to encrypt different fields in the same collection.要确保生产部署的安全,请同时使用基于角色的访问控制、静止加密、传输加密,以及可选的在用加密安全机制。请注意,不能同时使用客户端字段级加密和可查询加密来加密同一集合中的不同字段。
To learn more about Client-Side Field Level Encryption, see Client-Side Field Level Encryption Features.要了解有关客户端字段级别加密的更多信息,请参阅客户端字段级别的加密功能。
Scenario场景
The following fictional scenario demonstrates the value of Queryable Encryption in securing your application's data, and how Queryable Encryption interacts with the other security mechanism discussed in this guide.以下虚构场景演示了可查询加密在保护应用程序数据方面的价值,以及可查询加密如何与本指南中讨论的其他安全机制交互。
In this scenario, we secure sensitive data on a medical care management system that stores patients' personal information, billing information, and medical records for a fictional company, MedcoMD. 在这种情况下,我们保护医疗管理系统上的敏感数据,该系统存储虚构公司MedcoMD的患者个人信息、账单信息和医疗记录。None of the patient data is public, and specific data such as their social security number (SSN, a US government-issued ID number), patient ID number, billing information, and medication information are particularly sensitive and subject to privacy compliance. 没有任何患者数据是公开的,他们的社会安全号码(SSN,美国政府颁发的身份证号码)、患者身份证号码、账单信息和药物信息等特定数据特别敏感,需要遵守隐私规定。It is important for the company and the patient that the data is kept private and secure.数据的保密性和安全性对公司和患者都很重要。
MedcoMD needs this system to satisfy the following use cases:MedcoMD需要此系统来满足以下用例:
Doctors use the system to access patients' medical records, billing information, and update medications.医生使用该系统访问患者的医疗记录、账单信息和更新药物。Receptionists use the system to verify patients' identities using their contact information.接待员使用该系统通过患者的联系信息验证患者的身份。Receptionists can view a patient's billing information, but not their patient ID number.接待员可以查看患者的账单信息,但不能查看患者的身份证号码。Receptionists cannot access a patient's medical records.接待员无法访问患者的医疗记录。
MedcoMD is also concerned with the disclosure of sensitive data through any of the following methods:MedcoMD还关注通过以下任何方法披露敏感数据:
Accidental disclosure of data on a receptionist's publicly-viewable screen.接待员的公开屏幕上的数据意外泄露。Direct access to the database by a superuser such as a database administrator.由超级用户(如数据库管理员)直接访问数据库。Capture of data over an insecure network.通过不安全的网络捕获数据。Access to data by reading the database server's memory.通过读取数据库服务器的内存来访问数据。Access to data by reading database or backup files.通过读取数据库或备份文件访问数据。
What can MedcoMD do to balance the functionality and access restrictions of their medical care management system?MedcoMD可以做些什么来平衡其医疗保健管理系统的功能和访问限制?
Solution解决方案
MedcoMD uses the following security mechanisms to satisfy their use cases and protect against the disclosure of sensitive medical data:MedcoMD使用以下安全机制来满足其用例并防止敏感医疗数据的泄露:
Transport Encryption (TLS/SSL) to secure data as it travels over the network.传输加密(TLS/SSL),以确保数据在网络上传输时的安全。Encryption at Rest to protect against disclosure of data by reading database or backup files.静态加密,通过读取数据库或备份文件防止数据泄露。Role-Based Access Control to limit the access of database users to the collections necessary for them to perform their tasks.基于角色的访问控制,以限制数据库用户对执行任务所需的集合的访问。Encrypting sensitive fields with Queryable Encryption to satisfy the following use cases and constraints:使用可查询加密加密敏感字段,以满足以下用例和约束:Prevent reading data from server memory as the Queryable Encryption encrypted data is never on the database server in an unencrypted form.防止从服务器内存读取数据,因为数据库服务器上从未以未加密的形式存在可查询加密加密数据。Allow receptionists to verify patients' identities and prevent accidental disclosure of sensitive data on a receptionist's publicly viewable screen by providing receptionists with a client that is not Queryable Encryption enabled.允许接待员验证患者的身份,并通过向接待员提供未启用可查询加密的客户端,防止敏感数据意外泄露在接待员的公开屏幕上。Allow doctors to view sensitive data privately in their offices by providing doctors with a Queryable Encryption enabled client.通过为医生提供支持可查询加密的客户端,允许医生在办公室私下查看敏感数据。
Learn More了解更多信息
To view a list of security measures you should implement to protect your MongoDB deployment, see the Security Checklist.要查看为保护MongoDB部署而应实施的安全措施列表,请参阅安全检查表。
To start using Queryable Encryption, see the Quick Start.要开始使用可查询加密,请参阅快速入门。