KMS Providers
On this page本页内容
Overview概述Reasons to Use a Remote Key Management System使用远程键管理系统的原因Key Management Service Tasks关键管理服务任务Create and Store your Customer Master Key创建并存储客户主键Create and Encrypt a Data Encryption Key创建和加密数据加密键Supported Key Management Services支持的键管理服务Amazon Web Services KMS亚马逊网络服务KMSAzure Key VaultAzure键保管库Google Cloud Platform KMS谷歌云平台KMS- KMIP
Local Key Provider本地键提供程序
Overview概述
Learn about the Key Management Service providers Queryable Encryption supports.了解可查询加密支持的键管理服务提供商。
A Key Management Service is a Key Management System (KMS) provided as a service.键管理服务是作为服务提供的键管理系统(KMS)。
Reasons to Use a Remote Key Management System使用远程键管理系统的原因
Using a remote Key Management System to manage your Customer Master Key has the following advantages over using your local filesystem to host it:与使用本地文件系统托管客户主键相比,使用远程键管理系统管理客户主键具有以下优势:
Secure storage of the key with access auditing通过访问审核实现键的安全存储Reduced risk of access permission issues降低了访问权限问题的风险Availability and distribution of the key to remote clients键的可用性和向远程客户端的分发Automated key backup and recovery自动化的键备份和恢复Centralized encryption key lifecycle management集中的加密键生命周期管理
Additionally, for the following KMS providers, your KMS remotely encrypts and decrypts your Data Encryption Key, ensuring your Customer Master Key is never exposed to your Queryable Encryption enabled application:此外,对于以下KMS提供商,您的KMS可以远程加密和解密您的数据加密键,确保您的客户主键永远不会暴露在启用可查询加密的应用程序中:
- Amazon Web Services KMS
- Azure Key Vault
- Google Cloud KMS
Key Management Service Tasks关键管理服务任务
In Queryable Encryption, your Key Management Service:在可查询加密中,您的键管理服务:
Creates and encrypts the Customer Master Key创建并加密客户主键Encrypts the Data Encryption Keys created by your application加密应用程序创建的数据加密键Decrypts Data Encryption Keys解密数据加密键
To learn more about Customer Master Keys and Data Encryption Keys, see Keys and Key Vaults.要了解有关客户主键和数据加密键的更多信息,请参阅键和键库。
Create and Store your Customer Master Key创建并存储客户主键
To create a Customer Master Key, configure your Key Management Service provider to generate your Customer Master Key as follows:要创建客户主键,请按如下方式配置键管理服务提供商以生成客户主键:

To view a tutorial that demonstrates how to create and store a CMK in your preferred Key Management Service, see Tutorials.要查看演示如何在首选键管理服务中创建和存储CMK的教程,请参阅教程。
Create and Encrypt a Data Encryption Key创建和加密数据加密键
To create a Data Encryption Key:要创建数据加密键:
Instantiate a在启用可查询加密的应用程序中实例化ClientEncryptioninstance in your Queryable Encryption enabled application:ClientEncryption实例:Provide a提供一个kmsProvidersobject that specifies the credentials your Queryable Encryption enabled application uses to authenticate with your KMS.kmsProviders对象,该对象指定启用可查询加密的应用程序用于向KMS进行身份验证的凭据。
Create a Data Encryption Key with the在启用可查询加密的应用程序中,使用CreateDataKeymethod of theClientEncryptionobject in your Queryable Encryption enabled application.ClientEncryption对象的CreateDataKey方法创建数据加密键。Provide a提供一个dataKeyOptsobject that specifies with which key your KMS should encrypt your new Data Encryption Key.dataKeyOpts对象,该对象指定KMS应使用哪个键加密新的数据加密键。
To view a tutorial demonstrating how to create and encrypt a Data Encryption Key, see the following resources:要查看演示如何创建和加密数据加密键的教程,请参阅以下资源:
To view the structure of 要查看所有支持的KMS提供程序的kmsProviders and dataKeyOpts objects for all supported KMS providers, see Supported Key Management Services.kmsProviders和dataKeyOpts对象的结构,请参阅支持的键管理服务。
Supported Key Management Services支持的键管理服务
The following sections of this page present the following information for all Key Management Service providers:本页的以下部分为所有键管理服务提供商提供了以下信息:
Architecture of Queryable Encryption enabled client支持可查询加密的客户端的体系结构Structure ofkmsProvidersobjectskmsProviders对象的结构Structure ofdataKeyOptsobjectsdataKeyOpts对象的结构
Queryable Encryption supports the following Key Management Service providers:可查询加密支持以下键管理服务提供程序:
Amazon Web Services KMS亚马逊网络服务KMS
This section provides information related to using AWS Key Management Service本节提供了有关在启用可查询加密的应用程序中使用AWS键管理服务 in your Queryable Encryption enabled application.
的信息。
To view a tutorial demonstrating how to use AWS KMS in your Queryable Encryption enabled application, see Use Automatic Queryable Encryption with AWS.要查看演示如何在启用可查询加密的应用程序中使用AWS KMS的教程,请参阅使用AWS的自动可查询加密。
Architecture体系结构
The following diagram describes the architecture of a Queryable Encryption enabled application using AWS KMS.下图描述了使用AWS KMS的可查询加密应用程序的体系结构。
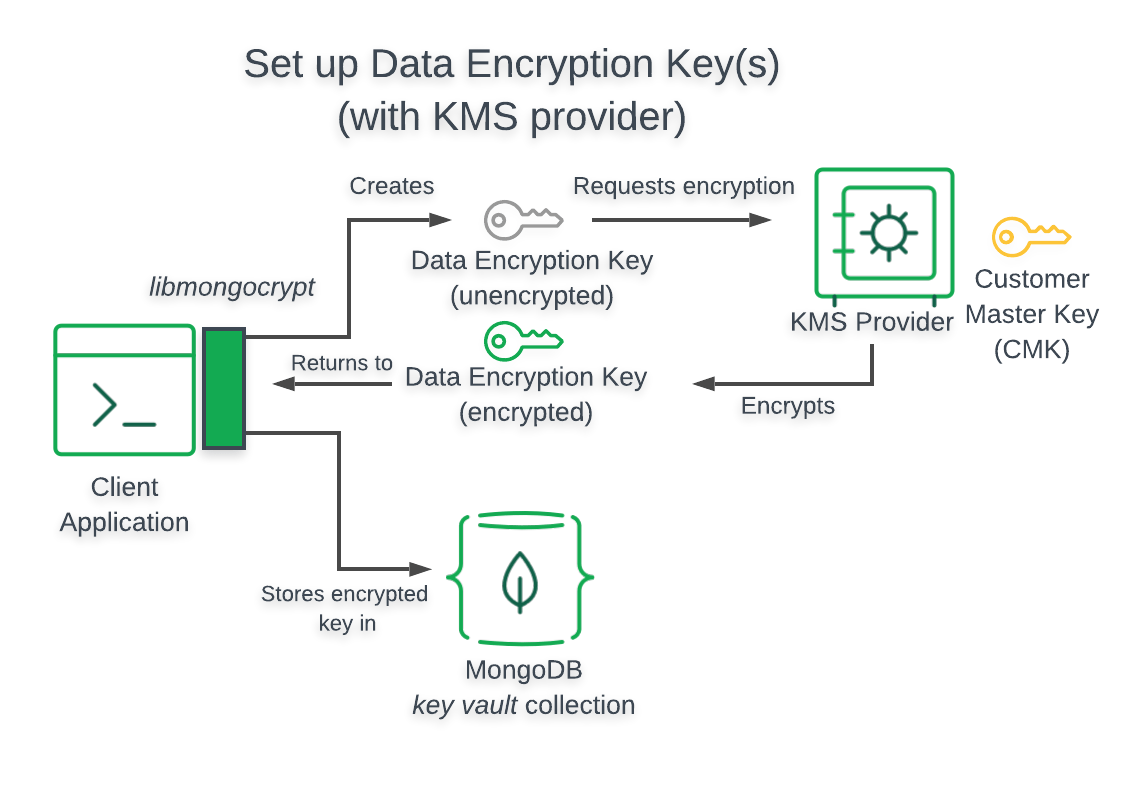
Client Can't Access Customer Master Key客户端无法访问客户主键
When using the preceding Key Management Service, your Queryable Encryption enabled application does not have access to your Customer Master Key.使用前面的键管理服务时,启用可查询加密的应用程序无法访问您的客户主键。
kmsProviders Object对象
The following table presents the structure of a 下表显示了AWS KMS的kmsProviders object for AWS KMS:kmsProviders对象的结构:
| Access Key ID | Yes | Yes | |
|---|---|---|---|
| Secret Access Key | Yes | Yes | |
| Session Token | No | Yes |
dataKeyOpts Object对象
The following table presents the structure of a 下表显示了AWS KMS的dataKeyOpts object for AWS KMS:dataKeyOpts对象的结构:
| key | Yes | |
|---|---|---|
| region | No | |
| endpoint | No |
Azure Key Vault键保管库
This section provides information related to using Azure Key Vault本节提供了有关在启用可查询加密的应用程序中使用Azure键保管库的信息。 in your Queryable Encryption enabled application.
To view a tutorial demonstrating how to use Azure Key Vault in your Queryable Encryption enabled application, see Use Automatic Queryable Encryption with Azure.若要查看演示如何在启用可查询加密的应用程序中使用Azure键库的教程,请参阅使用Azure的自动可查询加密。
Architecture体系结构
The following diagram describes the architecture of a Queryable Encryption enabled application using Azure Key Vault.下图描述了使用Azure键保管库启用可查询加密的应用程序的体系结构。

Client Can't Access Customer Master Key客户端无法访问客户主键
When using the preceding Key Management Service, your Queryable Encryption enabled application does not have access to your Customer Master Key.使用前面的键管理服务时,启用可查询加密的应用程序无法访问您的客户主键。
kmsProviders Object对象
The following table presents the structure of a 下表显示了Azure键保管库的kmsProviders object for Azure Key Vault:kmsProviders对象的结构:
| azure.tenantId | Yes | |
|---|---|---|
| azure.clientId | Yes | |
| azure.clientSecret | Yes | |
| azure.identityPlatformEndpoint | No | login.microsoftonline.com,仅用于非商业Azure实例,如政府或中国帐户。 |
dataKeyOpts Object对象
The following table presents the structure of a 下表显示了Azure键保管库的dataKeyOpts object for Azure Key Vault:dataKeyOpts对象的结构:
| keyName | Yes | |
|---|---|---|
| keyVersion | No | |
| keyVaultEndpoint | Yes | myVaultName.vault.azure.net |
Google Cloud Platform KMS谷歌云平台KMS
This section provides information related to using Google Cloud Key Management本节提供了有关在启用可查询加密的应用程序中使用谷歌云键管理 in your Queryable Encryption enabled application.
的信息。
To view a tutorial demonstrating how to use GCP KMS in your Queryable Encryption enabled application, see Use Automatic Queryable Encryption with GCP.要查看演示如何在启用可查询加密的应用程序中使用GCP KMS的教程,请参阅使用GCP的自动可查询加密。
Architecture体系结构
The following diagram describes the architecture of a Queryable Encryption enabled application using GCP KMS.下图描述了使用GCP KMS的可查询加密应用程序的体系结构。

Client Can't Access Customer Master Key客户端无法访问客户主键
When using the preceding Key Management Service, your Queryable Encryption enabled application does not have access to your Customer Master Key.使用前面的键管理服务时,启用可查询加密的应用程序无法访问您的客户主键。
kmsProviders Object对象
The following table presents the structure of a 下表显示了GCP KMS的kmsProviders object for GCP KMS:kmsProviders对象的结构:
| Yes | ||
| privateKey | Yes | -----BEGIN PRIVATE KEY-----\nyour-private-key\n-----END PRIVATE KEY-----\n your-private-key user-key.json credential file, you can extract the string by executing the following command in a bash or similar shell. user-key.json凭据文件,您可以通过在bash或类似的shell中执行以下命令来提取字符串。cat user-key.json | jq -r .private_key | openssl pkcs8 -topk8 -nocrypt -inform PEM -outform DER | base64 -w 0 |
| endpoint | No |
dataKeyOpts Object
The following table presents the structure of a 下表显示了GCP KMS的dataKeyOpts object for GCP KMS:dataKeyOpts对象的结构:
| projectId | Yes | |
|---|---|---|
| location | Yes | |
| keyRing | Yes | |
| keyName | Yes | |
| keyVersion | No | |
| endpoint | No | cloudkms.googleapis.com.cloudkms.googleapis.com。 |
KMIP
This section provides information related to using a KMIP本节提供了有关在启用可查询加密的应用程序中使用符合KMIP compliant Key Management Service provider in your Queryable Encryption enabled application.
的键管理服务提供程序的信息。
Architecture体系结构
The following diagram describes the architecture of a Queryable Encryption enabled application using a KMIP-compliant key provider.下图描述了使用符合KMIP的键提供程序的可查询加密应用程序的体系结构。
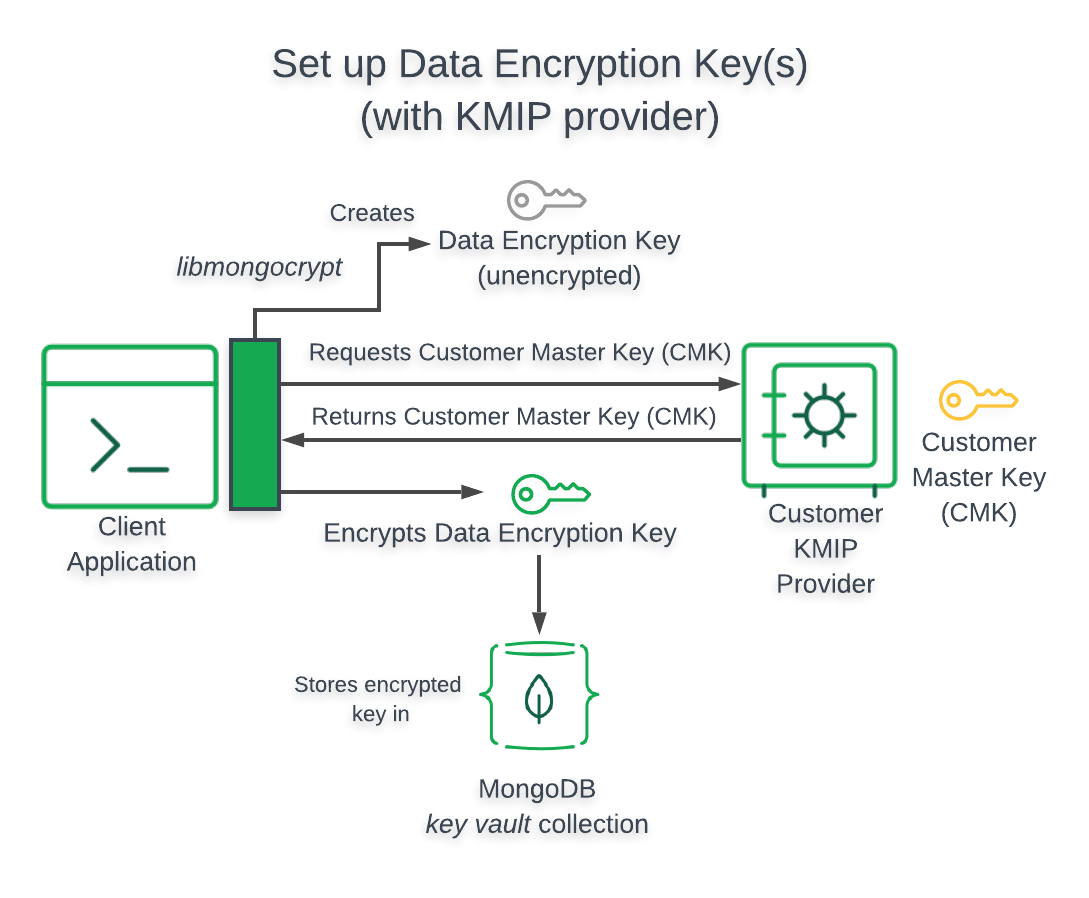
Client Accesses Customer Master Key客户端访问客户主键
When your Queryable Encryption enabled application uses a KMIP-compliant key provider, your application directly accesses your Customer Master Key.当启用可查询加密的应用程序使用符合KMIP的键提供程序时,您的应用程序将直接访问您的客户主键。
kmsProviders Object对象
The following table presents the structure of a 下表显示了符合KMIP的键管理服务的kmsProviders object for a KMIP compliant Key Management Service:kmsProviders对象的结构:
Authenticate through TLS/SSL通过TLS/SSL进行身份验证
Your Queryable Encryption enabled application authenticates through TLS/SSL when using KMIP.使用KMIP时,启用可查询加密的应用程序将通过TLS/SSL进行身份验证。
| endpoint | Yes |
|---|
dataKeyOpts Object对象
The following table presents the structure of a 下表显示了符合KMIP的键管理服务的dataKeyOpts object for a KMIP compliant Key Management Service:dataKeyOpts对象的结构:
| keyId | No | keyId field of a 96 byte Secret Data managed objectkeyId字段。keyId field in the masterKey document you send to your KMIP-compliant key provider, the driver creates a new 96 Byte Secret Data managed object in your KMIP-compliant key provider to act as your master key. masterKey文档中指定keyId字段,则驱动程序会在KMIP兼容的键提供程序中创建一个新的96字节秘密数据管理对象,用作您的主键。 |
|---|---|---|
| endpoint | Yes |
Local Key Provider本地键提供程序
This section provides information related to using a Local Key Provider (your filesystem) in your Queryable Encryption enabled application.本节提供了有关在启用可查询加密的应用程序中使用本地键提供程序(文件系统)的信息。
Do Not Use a Local Key File in Production在生产中不要使用本地键文件
A local key file in your filesystem is insecure and is not recommended for production. 文件系统中的本地键文件是不安全的,不建议用于生产。Instead, you should store your Customer Master Keys in a remote Key Management System相反,您应该将客户主键存储在远程键管理系统(KMS) (KMS).
中。
To learn how to use a remote KMS in your Queryable Encryption implementation, see the Tutorials guide.要了解如何在可查询加密实现中使用远程KMS,请参阅教程。
To view a tutorial demonstrating how to use a Local Key Provider for testing Queryable Encryption, see Quick Start.要查看演示如何使用本地键提供程序测试可查询加密的教程,请参阅快速入门。
Architecture体系结构
When you use a Local Key Provider, your application retrieves your Customer Master Key from the filesystem of the computer it runs on. The following diagram describes the architecture of a Queryable Encryption-enabled application using a Local Key Provider.使用本地键提供程序时,应用程序会从其运行的计算机的文件系统中检索客户主键。下图描述了使用本地键提供方启用可查询加密的应用程序的体系结构。
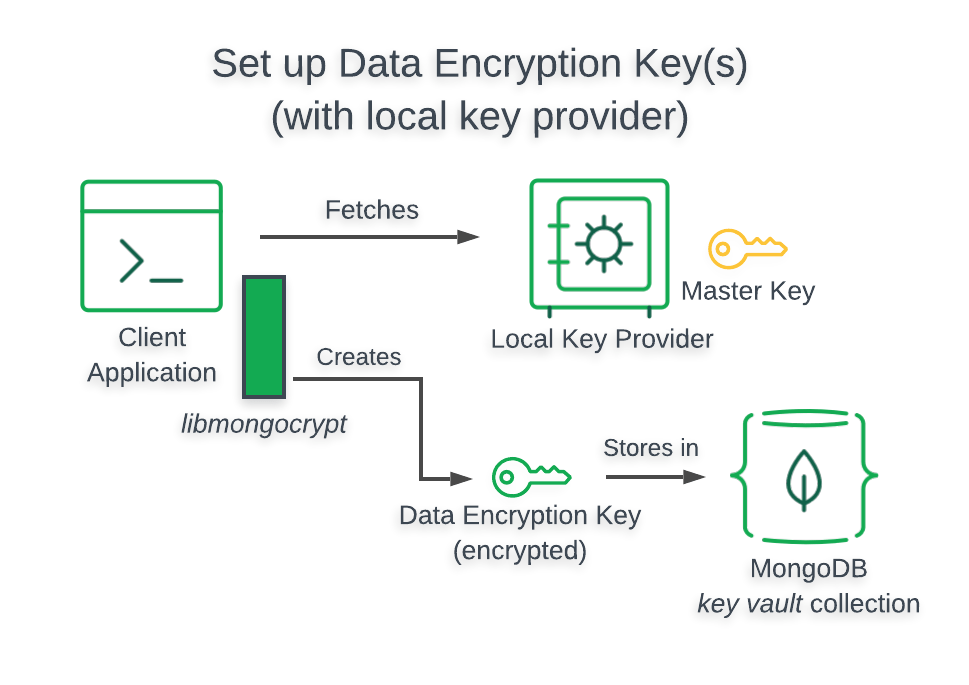
kmsProviders Object对象
The following table presents the structure of a 下表显示了本地键提供程序的kmsProviders object for a Local Key Provider:kmsProviders对象的结构:
| key | Yes |
|---|
dataKeyOpts Object对象
When you use a Local Key Provider, you specify your Customer Master Key through your 使用本地键提供程序时,可以通过kmsProviders object.kmsProviders对象指定客户主键。